Registered Sleepers
HIPAA compliant sleep study system. In use by hospitals all over the world, at all hours of the day, high availability and redundancy were keys for success. With FDA approved studies, cybersecurity is of the utmost importance.
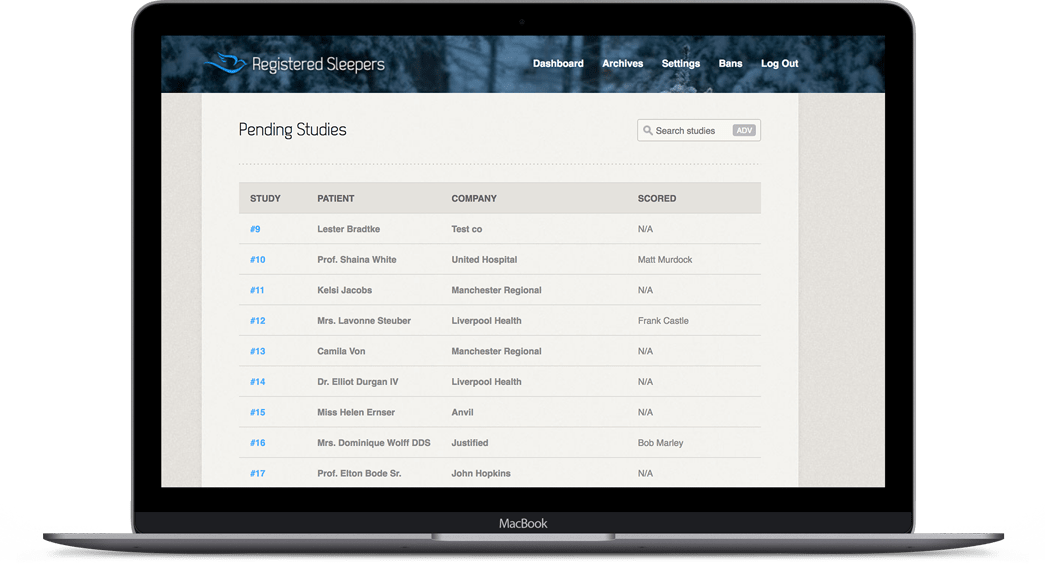
Since initial work in 2011, we have been updating the portal with the latest standards in software and DevOps, from intelligent auto-scaling upon traffic increases, to implementing secure downloads and uploads with Google Cloud.
This project has taught us so much along the way. When we first started, studies were using filesystem storage on a single machine. This led to slower downloads for those across the world and higher fail rates on data integrity checks. Moving to a hosted Cloud solution was the best decision we made.
Infinite Storage
We utilized the power of Google's Cloud platform to build a fault-tolerant way for studies to be stored indefinitely, without data corruption.
Security
Due to the nature of this application, we had to keep HIPAA compliance in mind at all times: full audit trails, denial of service prevention, and intrusion prevention.
High Availability
The portal is used by hospitals across the world. Running reliably, 24/7, with no issues, is a must. We haven't had a day of downtime since infrastructure improvements in 2013.
Software Development
Due to the sensitive medical information being stored, we focused much of our time on security and data integrity. Additionally, we conducted several audits to ensure compliance with HIPAA.
Security
In every application we build, security is at the forefront of our process. Security can't be an afterthought, especially when you're storing patient medical information. We ensure that all data is encrypted in transit and at rest.
Data Integrity
We implemented signed URLs for all study uploads and downloads from the system. This generates a unique URL for each download or upload request. These URLs are only good for one use, and they expire after a short period of time.
Auditing
The system monitors audit logs for various actions. Has a user been compromised? How many people have downloaded a study? Thanks to automated logging of all actions, statistics are made available instantly.
DoS Mitigation
Due to the sensitive nature of the data we are storing, we monitor the number of login attempts and watch for any unusual spike in activity. Further, we monitor all login attempts and do automated banning and rate limiting.

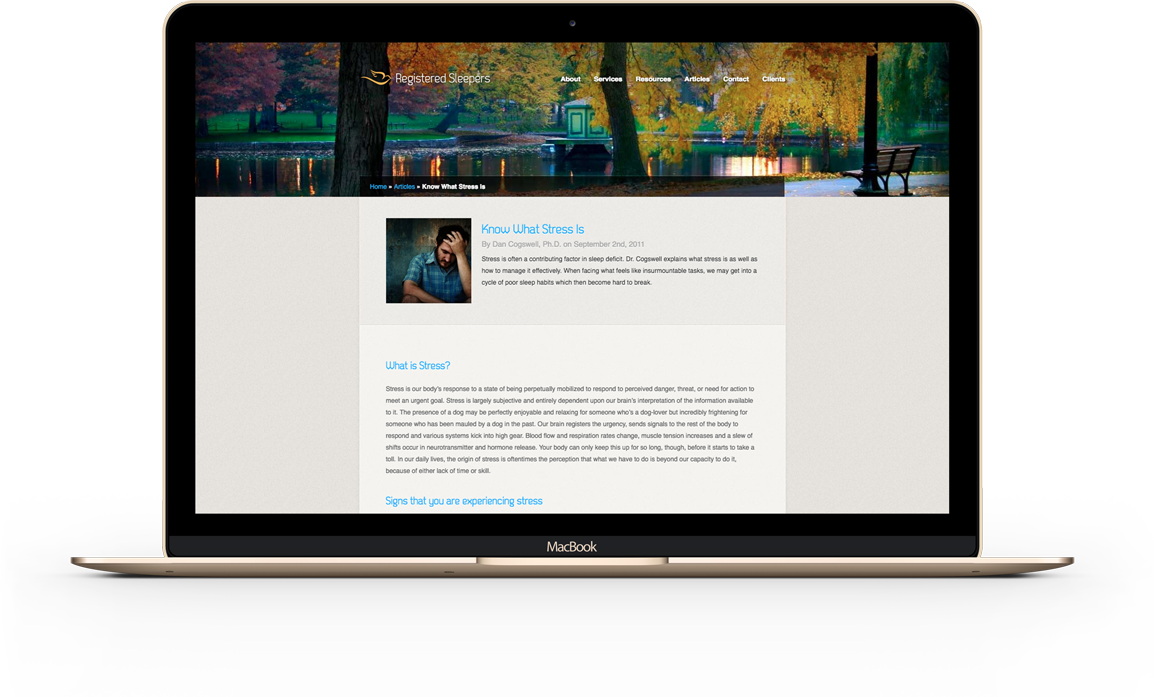
DevOps
You should be able to recreate your infrastructure at a moment’s notice. We utilized Ansible playbooks so that we can easily recreate our entire stack in minutes. Additionally, we put an intrusion detection and prevention system in place.
Firewall
We have strict firewall rules in place, to only accept connections over port 80 and 443. All other ports are closed. SSH access is key-based and only accessible over a non-standard port that is closed to the public.
Monitoring
We are able to monitor user actions as well as server resources. At set intervals, we manually look for suspicious activity so that less manual intervention is required when possible attacks happen in the future.
Redundancy
In this day and age, applications always need to be accessible. We simply can't afford outages. To mitigate this concern, we host the system across multiple data center regions and have load balancing between them.
Encryption
HIPAA requires all data to be encrypted at rest. We use Google Cloud Storage, which encrypts files as they are uploaded. Strict access policies are in place so that only those with permission can access, decrypt, and download studies.
12 Years
Our ability to partner with our clients for years is paramount to our success. Long-term relationships are key to our business.
30,000+
Countless studies have been scored using the portal. When it comes to an individual’s health, availability is key.
86+
Dozens of hospitals, companies, and organizations rely on the portal for scoring of sleep studies.
10,000+
Thousands of security threats have been mitigated using our firewall and intrusion detection and prevention systems.
Cybersecurity
In the world today, security can't be an afterthought. Security has to be a focus from the start. We took extra care to ensure that our bases were covered, and most importantly, that our clients are protected.
Regular Audits
This system undergoes regular internal, external, and automated security audits. This enables us to be proactive, not just reactive. Additionally, we consistently audit our infrastructure to make sure that all patches and updates are applied.
Logging
Consolidation of logs across various services is extremely important. This lets us run queries against all activity occurring on the system to determine if any attacks are in progress or have been attempted in the past.
Penetration Testing
Our software undergoes automated static and dynamic code analysis prior to deployment. As a result, there are no easily exploitable vulnerabilities. Additionally, we conduct professional penetration testing on the application.
Password Requirements
In order to remain HIPAA compliant, we've implemented strict password requirements. We have no max password length, but we require a minimum of 8 characters. Additionally, all passwords must be changed every 90 days.
I can't recommend Jacob and Encryption highly enough. I have been working with them for years. They really care about my business and want to help. I know that I can call them day or night and that they have my back. I trust and rely on them to run my business.

Life is full of problems and challenges. Let us help you get through it.